Ing. Fabio ROMANI and Dr. Yassine FATAH
 Ing. Fabio ROMANI is Chief Executive Officer of IPS S.p.A, a leading company in the Cyber Intelligence sector. IPS operates in around 30 Countries aiding Law Enforcement Agencies and Police Departments on a daily basis.
Ing. Fabio ROMANI is Chief Executive Officer of IPS S.p.A, a leading company in the Cyber Intelligence sector. IPS operates in around 30 Countries aiding Law Enforcement Agencies and Police Departments on a daily basis.
Dr. Yassine FATAH, Product Specialist of IPS S.p.A and Instructor for IPS Academy. The Academy hosts more than one hundred training days and advanced technical lessons for thousands of Police Officers every year
Cyber security, by definition and by interpretation, provides for a series of defensive measures to safeguard strategic assets from cyber-attacks of various kinds. This vision is similar to the medieval concept of building defensive walls ever higher and thicker to protect the perimeter. Since we will be facing a continuous chase between breaches and reconstructions, a paradigm shift in the approach and concept of IT security itself is the key to making sensitive assets safer.
Staying passive and rebuilding where there has been a breach and learning attack techniques only after having suffered them brought influential dynasties to ruin during the raids on the European continent of the Norsemen first and the Mongols later at the start of the previous millennium. The truly innovative approach came when the primordial concept of Intelligence was born. Knowing in advance when, in what way, and with which tools the structures will be attacked allows to efficiently prevent and mitigate such attempts. This approach is defined today as Cyber Threat Intelligence, which is the systematic and continuous scanning of the Web, Social Networks, Dark Web, and Forums in search of potential threats, even before they can manifest themselves. Having a team of informants, defined in the corporate sphere as analysts, who know the language of the attacker, the tools he uses, and at what time he intends to perpetrate the attack, demonstrates a proactive approach to the security of physical assets. With digital assets (which also control physical ones) the situation is very similar. The SOC department that is updated in near-real-time on the methods and timing of attacks received by similar organizations can impose and organize the necessary defense measures in advance.
Cyber Threat Intelligence can be arranged as an internal activity within the organization or it can also be delegated to an external professional service. The purpose of this article is to analyze the main information sources useful to the CTI and report the main advantages of an internal or external approach to intelligence activities.
There are many data collection methods from a Cyber Threat perspective, but for companies (more than for institutions) it is essential that these fall within the framework of Open-Source Intelligence. The topic has been dealt with on several occasions, so in short, OSINT is the collection and analysis of data starting from public or publicly shared sources to take advantage of it. In this sense, OSINT aims to bring out concrete or potential threats to the physical or cybernetic perimeter of the reality to be protected. Concerning the investigative approach, the methods and rules change, but not the vastness of the pool of data to be analyzed and therefore the need to use a research approach supported by technology. Going in order, let’s analyze the most common open information resources that provide potentially valuable information.
Probably the most obvious source, and in a certain sense also overrated, is the dark web. On the dark web you can find, in various forms, data breaches, botnets, vulnerabilities, and classified documents which, directly or indirectly, may have as their object the dynamics of the company or state organization for which the analyst is carrying out the research. It can be considered, in a certain way, an overrated resource, as more and more often sensitive information, malware, and data breaches for sale are offered in forums and social networks where sales are faster, more efficient and a greater audience of possible buyers can be reached. Today we have arrived at the concept of cybercrime as-a-service for which the development of malware is not aimed at a specific attack, but has a commercial purpose. This sealed-compartment criminal model generates an additional level of difficulty in post-attack reverse engineering activities. The microservices model with anonymous sales on the dark web, on forums, and on Telegram makes the development of techniques efficient as each organization specializes in the sector where it is more functional, making the chain of events very fragmented. Now let’s see in detail the different sources of vulnerabilities and services offered.
A data breach that reports a user’s login credentials is one of the most serious vulnerabilities, as well as one of the most common. Often users use their work email to sign up for services for personal use which, if attacked, can seriously compromise the users’ data. It is rare, during various activities, including preventive ones, to find organizations without employees whose credentials had been subject to data breaches in the past, from the smallest companies to secret services agencies. Once exposed, the credentials can be used to access the company network, mail server, and administrative portal. Even if the credentials have been changed or the employee uses a two-factor authentication app, passwords say a lot about their creator and are often used as a Social Engineering tool. For example, the password “giulia2203”, even if it is not in use anymore because it is obsolete, associated with the employee’s name provides a strong starting point for the attacker.
Consequently, someone who is interested in penetrating an organization’s network could use a profile or a fake email to infect the employee’s smart working station to then initiate ransomware from within. The same password could then be used as a search criterion and highlight other emails connected to the targeted employee.
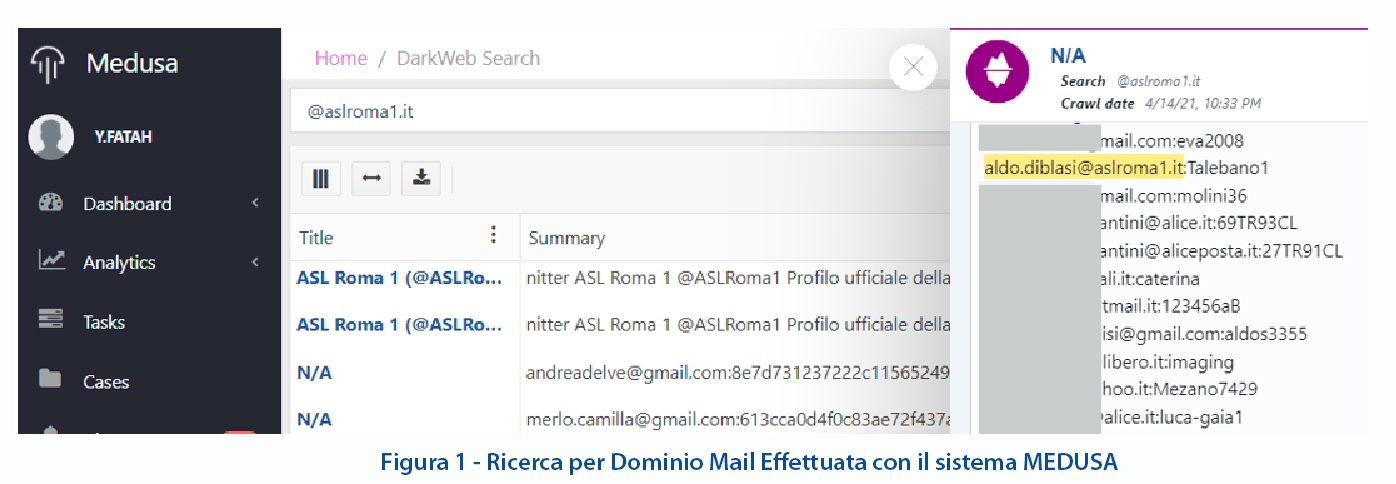
Figure 1 – Email Domain Research was done using the MEDUSA system
Botnets are networks of compromised PCs or phones that are used for various reasons. Just like data breaches, they are for sale on the dark web and can be used for several purposes. In the best-case scenario, a network of PCs and smartphones infected by the same agent can contribute to the computational capacity of a miner, so a small part of the CPU (or APU) is dedicated to “remote” cryptocurrency mining. In the worst-case scenario, botnets can be used to launch DDoS attacks, Distributed Denial of Service, to block sensitive equipment to put the IT structure of an organization in jeopardy. Lastly, they can contribute to lowering the level of security if some of the organization’s devices are the subject of shared malware. We talk about malware since at the base of botnets there is a malicious code, often a Zero-day vulnerability used without any particular purpose, but to infect the greatest number of devices. It is important to note that those who create the malware do not always coincide with the actors who then launch the attacks and rarely do the two categories coincide with the users of the botnet. Criminal organizations work on different levels, specializing in the sections of the chain of events that lead to the final result.
Vulnerabilities are criticalities in the code of an application that can be exploited as flaws to enter a system. The vulnerabilities concern both proprietary and third-party software and often operating systems as well. These are called Zero-day vulnerabilities if not known and are particularly sought after as they usually allow for undisturbed and relatively longer-lasting access.
These “products” are sold, along with classified documents, to ransomware and other services on the dark web. The criticality of this source lies precisely in its nature. It is rare to make a certified purchase and one often falls into scams. To overcome this problem, escrow services have been created that act as intermediaries between customer and supplier. It has been noted that the aforementioned activities have progressively moved to other sources for some reason considered more reliable such as Telegram and specialized forums.
As for the instant messaging app, groups and channels provide a lot of relevant information. It is enough to type on Google a banal chain of operators to have access to an infinite database of vulnerabilities, data breaches, and the most sensitive you are looking for. The most curious reader will try to search the search engine for the string site: t.me intext: “CVE” or the string site:t.me intext:”log4j” and will immediately understand the scope of the Telegram phenomenon from a Cybersecurity and Cyber Threat Intelligence perspective.
There are many specialized forums on the web, but special mentions go to Raidforums and Reddit. The first functions as a marketplace and source of information while the second, a cross-sectional social network, is used as a showcase for particular actions and a source of specialized information.
Finally, we can mention Pastebin, a site that is used as an anonymous recycle bin (Pastebin means precisely recycle bin) where information of value for the public domain is stored. It does not have a real search interface, so the data can only be used by search operators. It could therefore be interesting to search for the site:pastebin.com intext:password intext:gov.
This non-exhaustive list of sources for the Cyber Threat Intelligence analyst makes it clear that working manually is complicated and time-consuming. We are therefore faced with the need to automate the extrapolation work to improve the ability to assess and search for threats. These automatisms can be carried out in two ways:
- using an Open-Source Intelligence platform correctly set up for targeted data collection and equipped with appropriate research tools and graphic visualization;
- using an external consultancy service, or a platform where the analyst will only have to research parameters, and the research and analysis work will be done upstream by a team of researchers.
Both solutions have advantages and disadvantages. Probably a private organization could tend to use in the cloud a turnkey service customized by a team of external analysts, while a government organization might prefer to independently manage an on-premises data collection tool using its analysts and specialists. Furthermore, the company must always combine economic reasons with regulations on personal data, while a governmental body has potential access to a series of specific information that it may wish to combine with open-source data extracted with a Cyber Threat Intelligence analysis.
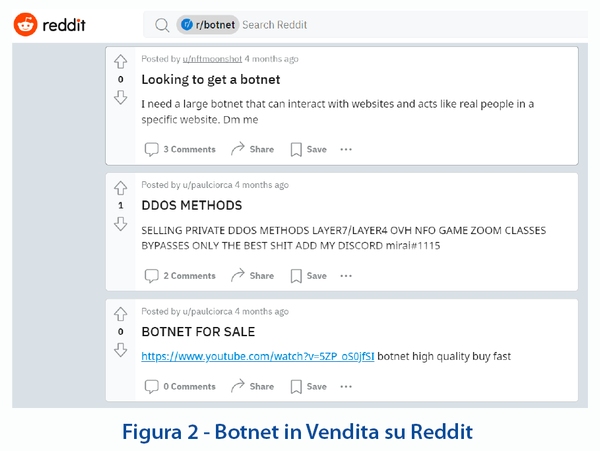
Figure 2 – Botnet on sale on Reddit
As highlighted in this short article, passive defense is a model that cannot keep up with the new challenges in the security field; not even firewalls and antivirus have remained anchored to a purely passive approach as the latest models and updates include active threat filtering and Machine Learning functions. Therefore, a 360-degree proactive model is needed, supported by an active threat search mechanism, which analyzes public sources and near-real-time news in a systematic and automated manner. Being aware of attacks perpetrated on nearby realities can be the keystone in the dynamic defense of digital assets, together with all the other now mandatory measures in the field of IT security such as two-factor authentication, training, and awareness of employees.
The current geopolitical situation in Eastern Europe reflects a lot of the themes proposed in this article. Modern cyberattack techniques are an integral and fundamental part of what is called cyber warfare. Anonymous’ attack on Russian strategic assets was emblematic. It was an attack with a combination of several techniques, including DDoS, exploiting botnets with endpoints distributed in different countries, and online propaganda. Cyberwarfare has become so integrated into the development of military strategies that it has taken on a deterrent value. Today the potential damage that can be dealt with by cyber-attacks to strategic assets such as power plants, gas pipelines, hospitals, and military infrastructures is calculated in offensive and defensive strategies, both in peacetime and in times of conflict. Investing in training, awareness-raising and a proactive approach at every level can make a difference today in terms of defending corporate assets, but also, as we have seen, in terms of national security.




